Dell Switch Configuration Commands
- Connect using Serial Cable
- Save Configuration
- Configuring Management Interface IP
- Configuring Host Name
- Enabling SSH Server
- Enable Simple L2 Switching
- Configuring a Range of Interfaces
- VLANs Configuration
- Show Connected Devices
- Show Config
- Breakout Ports
- OpenFlow Configuration
Connect using Serial Cable
# Check the baud rate of the switch
# It is usually 9600 or 115200
sudo screen /dev/ttyS0 115200
# Later to connect to previous screen session
sudo screen -x
Save Configuration
enable
copy running-config startup-config
Configuring Management Interface IP
enable
configure
interface managementethernet 1/1
ip address <ip address>/<cidr>
no shutdown
Configuring Host Name
enable
configure
hostname <host_name>
Enabling SSH Server
enable
configure
ip ssh server enable
Create an account
enable
configure
username <username> password 0 <password>
Create enable Secret
enable
configure
enable password 0 <password>
Enable Simple L2 Switching
enable
configure
interface gigabitethernet 1/<port number>
switchport
no shutdown
Configuring a Range of Interfaces
interface range gigabitethernet 1/<start-port>-1/<end-port>
# Example:
interface range tengigabitethernet 1/3/1-1/3/4
VLANs Configuration
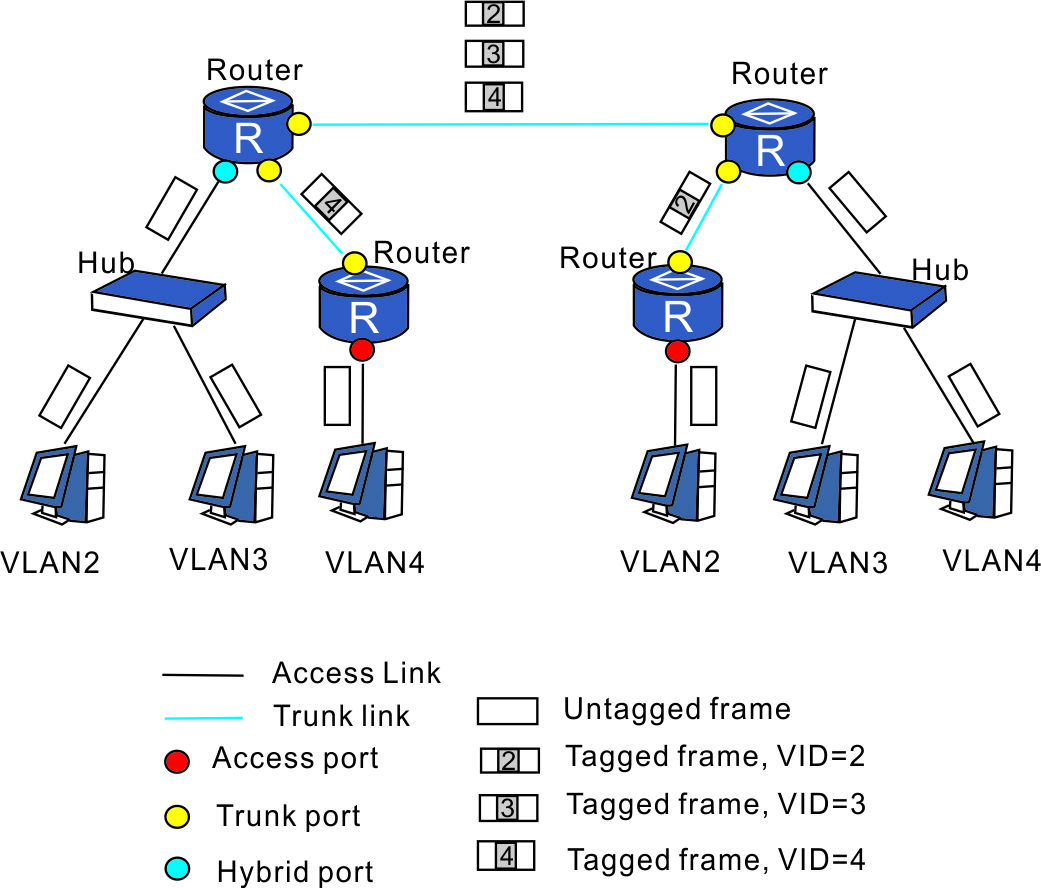
There are a few rules:
- A port can be untagged to MAX one VLAN and at least one VLAN, only one VLAN in another word.
- A port can be tagged to multiple VLAN at the same time.
- A port can’t be tagged and untagged to the same VLAN.
Types of VLAN Port
- Aceess: Part of only one VLAN (usually default vlan i.e. VLAN 1)
- Hybrid: Allow multiple VLANs through. Multiple tagged and untagged VLANs are allowed.
- Trunk: Allow multiple tagged VLANs through.
PLAN (Private VLAN) VLANs are used to isolate users in different subnets usually. However, PVLAN is used to isolate users in the same subnet. ISPs uses PVLAN to prevent their users reach to each other.
# ---- [Listing VLANs]
enable
show vlan
# ---- [Creating VLANs]
enable
configure
interface vlan <new VLAN ID>
# ---- [Adding ports to VLAN]
enable
configure
interface vlan <VLAN ID>
untagged gigabitethernet 1/<port number>
untagged gigabitethernet 1/45-1/48
no untagged gigabitethernet 1/<port number>
# Then add to a vlan either tagged ot untagged
Real Example: Trunk Port Setup
I was at the data center recently, trying to establish a connection to the
network A.B.C.D/X through Switch A. This network is accessible only through tagged VLAN 2500.
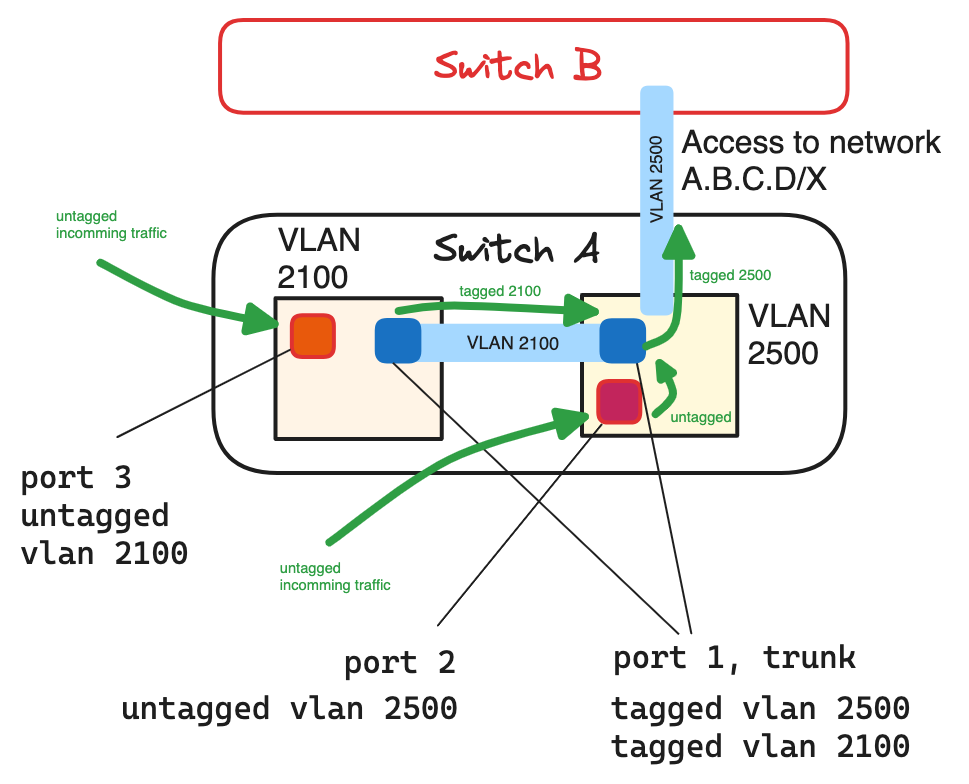
The Setup:
Port 1on Switch A needs to be a trunk port, allowing it to carry multiple tagged VLANs:2100and2500. This trunk port can send and receive traffic from both VLANs while maintaining their tags.Port 2is an access port that should be untagged for VLAN2500. This means it will handle traffic without tags, adding the VLAN2500tag to outgoing traffic and removing it from incoming traffic.Port 3is an access port that belongs to VLAN2100. Traffic from devices connected to this port is untagged when it entersSwitch A.
Traffic Flow:
Port 3 (VLAN 2100): Traffic from a device connected to port 3 enters Switch A as untagged.
Since port 3 is associated with VLAN 2100. When this traffic needs to access network A.B.C.D/X,
Switch A sends it out through port 1 as both are member of same VLAN 2500.
Port 1 re-tags the traffic with VLAN 2500 before sending it to the network A.B.C.D/X.
Port 2 is set as an untagged member of VLAN 2500, Switch A processes this traffic as part of VLAN 2500.
When it exits through port 1, it is tagged with VLAN 2500 and sent to Switch B, destined for the network A.B.C.D/X.
# port 1
enable
configure
interface TenGigabitEthernet 1/1
switchport
switchport mode private-vlan trunk
# port 2, 3
enable
configure
switchport
# vlan 2100
enable
conf
interface vlan 2100
untagged TenGigabitEthernet 1/3
tagged TenGigabitEthernet 1/1
# vlan 2500
enable
conf
interface vlan 2500
tagged TenGigabitEthernet 1/1
untagged TenGigabitEthernet 1/2
Show Connected Devices
show mac-address-table
Show Config
show interfaces status
show interfaces configured
show interfaces switchport
show running-config
# For an Interface:
interface twentyFiveGigE 1/3/1
show config
Breakout Ports
show system stack-unit 1 fanout configured
stack-unit <stack number> port <port number> portmode <mode> speed <speed>
# Example with no:
no stack-unit 1 port 3 portmode quad
#<stack number>: 1-6
#<port number>: 1/2
#<mode>: {dual, quad, single}
#<speed>: {100G, 40G, 10G}
# Example:
stack-unit 1 port 1/2 portmode single speed 40G
Example:
- 1x100G: single and 100G
- 1x40G: single and 40G
- 2x50G: dual and 50G
- 4x10G: quad and 10G
- 4x25G: quad and 25G
Set an interface to default settings:
default interface twentyFiveGigE 1/3/3
OpenFlow Configuration
Dell(conf)#openflow of-instance 1
Dell(conf-of-instance-1)#controller 1 10.11.54.60 tcp sndbuf 32000
Dell#show openflow of-instance 1
Instance : 1
<snipped>
Controller 1 : TCP, 10.11.54.60/6633, rcv/sndbuf 2000/32000, not-connected
Controller 2 : -
openflow of-instance 1
controller 1 192.168.10.10 tcp
of-version 1.0
dpid-mac-addr 00:00:00:01:00:52
no shutdown
cam-acl default
cam-acl-vlan default
That’s it!
Want to read more?
Check out these pages:- Kubebuilder Admission Webhook for Core Types
- Kubernetes Object Configuration with Kustomize
- A Guide to CA, CSR, CRT, and Keys (Digital Certificates)
- Deploy a Local Kubernetes Webhook Server
- Linux iptables Reference Guide with Examples
- Configuring sFlow on Dell Switch with OS9
- Configuring WebDAV Access for Zotero on Ubuntu
- Route Traffic through a Private Network using Dynamic Port Forwarding and Proxy SwitchyOmega
- Access to the SAVI using CLI
- Connect to Existing Running Desktop Session using x11vnc
- Install Ubuntu 20.04 via PXE UEFI Setup
- Access to the SAVI using Web Portal
- Run PyCharm IDE over SSH using Remote Host Interpreter
- Reverse SSH to Access Hosts Behind the NAT
- VNC Server in Ubuntu 16.04, 18.04 and CentOS 7
- Create an Overlay Network in Ubuntu using Open vSwitch (OVS)