Configuring sFlow on Dell Switch with OS9
Getting Started
sFlow is a traffic monitoring technique that collects and analyzes traffic statistics based on packets (therefore it is highly scalable). It provides complete traffic information from Layer 2 to Layer 4 (source).
In some instances, like with Z9100 and S4048 Dell switches, only sFlow is supported for exporting network traffic data. Let’s take a look how we can configure sflow on OS9.
Configure Networking
There are two important players: sFlow agent and sFlow collector. The agent is responsible for generating sFlow, while the collector’s role is to gather and handle sFlow data. Collector should be reachable by the switch. You may assign an IP to the interface connected to the collector and then access the collector IP address. You cannot use the management port to export sflow data.
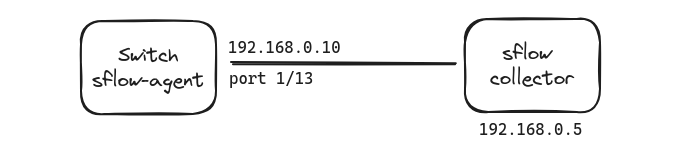
Assume you have a collector with an interface with IP 192.168.0.5/24 connected to port 1/13 of the switch. Then, in the switch:
> conf
> interface twentyFiveGigE 1/13
> (conf) ip address 192.168.0.10/24
> (conf) no shutdown
The switch is now ready to send sflow data to the collector.
Configure SFLOW
First take a look at the configuration:
> show sflow
sFlow services are disabled
Egress Management Interface sFlow services are disabled
Global default sampling rate: 32768
Global default counter polling interval: 20
Global default extended maximum header size: 128 bytes
Global extended information enabled: switch
0 UDP packets exported
0 UDP packets dropped
0 sFlow samples collected
Configure sflow:
> conf
> sflow enable
# sflow collector ip: 192.168.0.10
# sflow agent (switch) ip: 192.168.0.5
# port the collector listens: 6343
> sflow collector 192.168.0.5 sflow-agent 192.168.0.10 6343
> sflow extended-switch enable
Once you enable sFlow services, you need to enable sFlow per interface from which you wish to receive sFlow data:
> conf
> (conf) interface twentyFiveGigE 1/15/1
> (conf) sflow enable # sflow for egress traffic
> (conf) sflow ingress-enable # sflow for ingress traffic
Redirect sFlow Traffic to Another Host
Sometimes, the final consumer or collector of sFlow data may not be conveniently reachable directly from the switch. In such cases, one effective method to bridge the gap is by leveraging iptables::
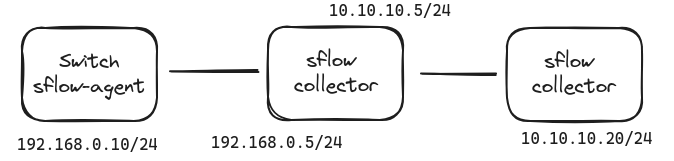
sudo iptables -tnat -A PREROUTING -i eth0 -p udp --dport 6343 \
-j DNAT --to-destination 10.10.10.20:6343
sudo iptables -tnat -A POSTROUTING -d 10.10.10.20/32 -j SNAT --to 10.10.10.5
Want to read more?
Check out these pages:- Kubebuilder Admission Webhook for Core Types
- Kubernetes Object Configuration with Kustomize
- A Guide to CA, CSR, CRT, and Keys (Digital Certificates)
- Deploy a Local Kubernetes Webhook Server
- Linux iptables Reference Guide with Examples
- Configuring WebDAV Access for Zotero on Ubuntu
- Dell Switch Configuration Commands
- Route Traffic through a Private Network using Dynamic Port Forwarding and Proxy SwitchyOmega
- Access to the SAVI using CLI
- Connect to Existing Running Desktop Session using x11vnc
- Install Ubuntu 20.04 via PXE UEFI Setup
- Access to the SAVI using Web Portal
- Run PyCharm IDE over SSH using Remote Host Interpreter
- Reverse SSH to Access Hosts Behind the NAT
- VNC Server in Ubuntu 16.04, 18.04 and CentOS 7
- Create an Overlay Network in Ubuntu using Open vSwitch (OVS)